In an era defined by persistent cyberattacks, insider threats, and growing cloud adoption, Zero Trust Architecture (ZTA) has emerged as a leading security paradigm. But despite its growing popularity, many IT leaders still wonder: Is Zero Trust just the latest marketing buzzword, or is it truly the future of cybersecurity?
Let’s explore what makes Zero Trust a transformative framework—and why it may be essential for building resilient, future-ready enterprise security.
Zero Trust is not just a security model—it’s a mindset shift. First introduced by Forrester Research in 2010, the Zero Trust model challenges the long-held assumption that everything inside an organization’s network can be trusted. Instead, it operates on a strict “never trust, always verify” principle.
Unlike traditional perimeter-based defenses, which implicitly trust users and devices once they’re inside the network, Zero Trust assumes that no user or system—internal or external—should be trusted by default. Every request for access must be authenticated, authorized, and continuously validated based on context such as identity, location, device health, and behavior.
Think of Zero Trust like airport security. Just because you’re inside the terminal doesn’t mean you can walk onto any plane. At every gate, your boarding pass and ID are re-checked to ensure you’re authorized to be there. Similarly, in a Zero Trust environment, users and devices are continuously verified before being granted access to any digital resource.
With hybrid work becoming permanent and workloads distributed across multiple clouds and SaaS apps, the traditional network boundary no longer exists. According to Gartner, by 2025, 60% of organizations will phase out VPNs in favor of Zero Trust access solutions.
Zero Trust reduces the risk of lateral movement and insider abuse by limiting users’ access to only the resources they truly need. Behavioral analytics also play a vital role in detecting anomalies.
Frameworks such as HIPAA, PCI-DSS, and ISO 27001 now encourage Zero Trust principles. Organizations adopting ZTA can more effectively enforce auditable security policies, which simplifies compliance.
Zero Trust is not a product—it’s a strategic approach. Unfortunately, vendors often use the term as a catch-all for any modern security tool. This has led to confusion and skepticism. However, organizations that implement Zero Trust holistically—integrating identity, endpoint security, and network segmentation—report faster threat detection, reduced attack surface, and better breach containment.
🔍 Industry Insight: A study by IBM found that Zero Trust adopters reduced the average cost of a data breach by $1.76 million compared to those without it.
Implementing a Zero Trust architecture is not about a single product—it’s an ecosystem of technologies that work in concert to enforce identity verification, access control, behavioral monitoring, and continuous threat containment. Below are the core technologies that power a mature Zero Trust framework:
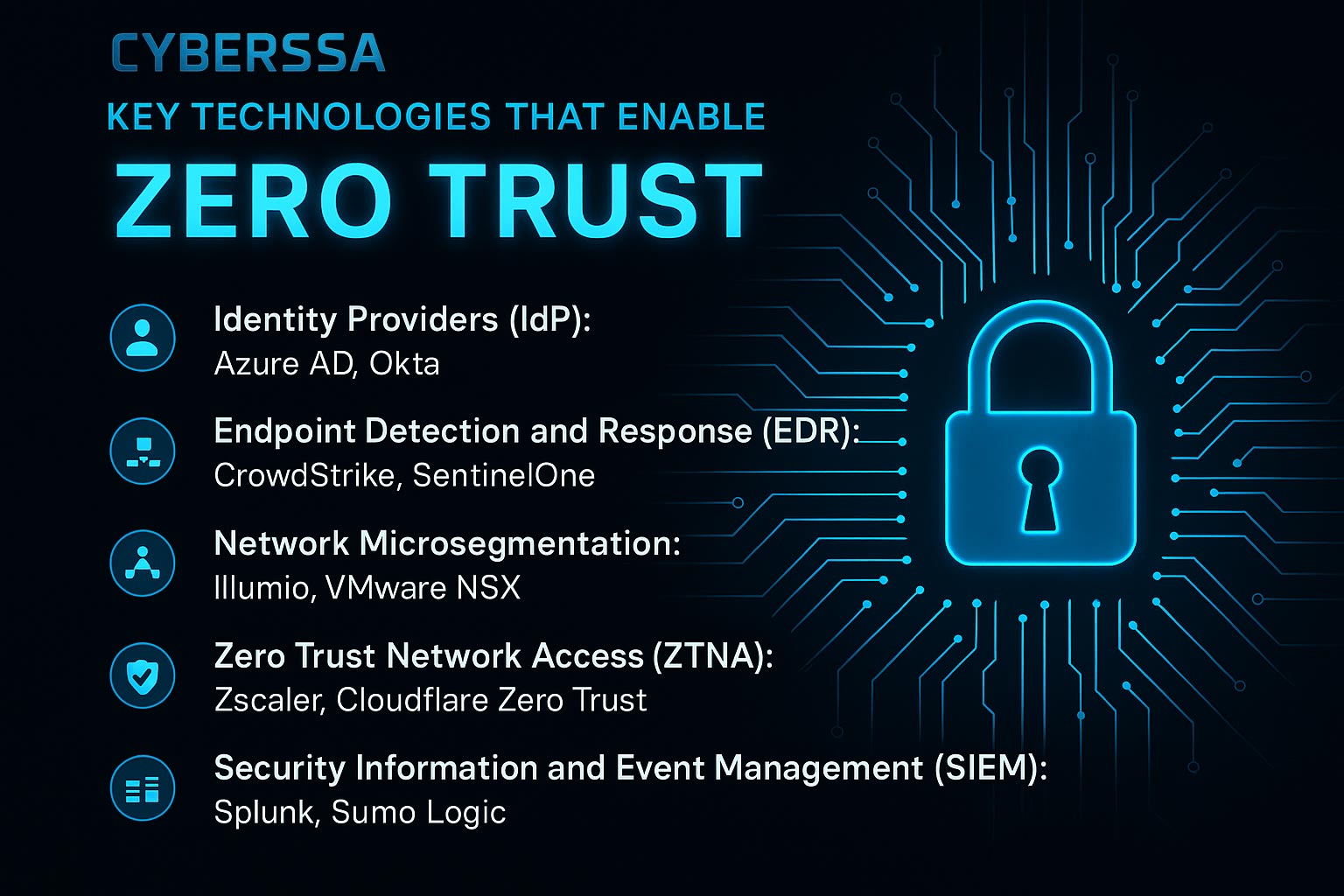
🔹 Examples: Azure Active Directory (Azure AD), Okta
IdPs are central to verifying user identities and enforcing authentication policies. They support features like single sign-on (SSO), multi-factor authentication (MFA), and role-based access control (RBAC), which are critical in a Zero Trust environment.
📌 Real-world example: When a remote employee attempts to access a company dashboard, Azure AD evaluates the login context (device, location, time). If the behavior seems unusual, it triggers an MFA challenge or blocks the request entirely.
🔹 Examples: CrowdStrike Falcon, SentinelOne
EDR tools continuously monitor endpoint behavior, detect malicious activity, and provide automated threat response. In a Zero Trust model, device health and compliance are critical criteria for granting access.
📌 Real-world example: If SentinelOne detects that a user’s laptop is exhibiting ransomware-like behavior (e.g., mass file encryption), it can automatically isolate the device from the network and alert the SOC team via the SIEM.
🔹 Examples: Illumio, VMware NSX
Microsegmentation breaks the network into granular segments, allowing organizations to enforce least-privilege access between workloads. Even if an attacker breaches the perimeter, they can’t move laterally across the environment.
📌 Real-world example: A compromised web server can’t reach the database layer because Illumio enforces strict communication rules between segments, significantly reducing attack surface.
🔹 Examples: Zscaler Private Access, Cloudflare Zero Trust
ZTNA solutions provide secure, context-aware access to internal applications without exposing them to the public internet. They verify users, devices, and access context before connecting to each resource.
📌 Real-world example: Instead of giving VPN access to the entire network, Cloudflare Zero Trust allows an employee to connect only to the HR system, using browser-isolated, identity-authenticated sessions.
🔹 Examples: Splunk, Sumo Logic
SIEM platforms aggregate logs, telemetry, and alerts from across the Zero Trust stack. They enable real-time detection, threat correlation, and incident investigation, often augmented with SOAR (Security Orchestration, Automation, and Response).
📌 Real-world example: Splunk ingests data from Okta, SentinelOne, and Illumio, identifying an anomalous login followed by suspicious file access—triggering an automated investigation workflow.
While the term “Zero Trust” is certainly trending, its underlying principles are not new—and they are more relevant than ever in our hyper-connected world. Zero Trust is not a quick fix, but a journey. Organizations that approach it strategically will be better equipped to handle future threats and compliance challenges.
At CYBER SSA, we help organizations build and mature their Zero Trust programs using a layered, standards-based approach. Our team integrates advanced detection tools, identity-driven security, and expert threat hunting to make Zero Trust achievable—without disrupting your operations.
Whether you’re starting with identity governance, micro-segmentation, or advanced telemetry monitoring, CYBER SSA provides tailored Zero Trust implementation roadmaps designed for your unique industry and risk profile.
Ready to evolve beyond the perimeter?
Let CYBER SSA help you take the first step into the future of secure enterprise architecture.
Fill out the form below and we will get back to you within the next 24
hours to complete the order, and then you’re all set to get started!